Modern authentication is no longer tied to a single application.
Organizations use multiple cloud, SaaS, partner, and internal systems, all requiring a secure, shared identity. Federated identity and Single Sign-On (SSO) address this by letting trusted identity providers handle authentication, enabling seamless access across apps.
The two main SSO standards are OpenID Connect (OIDC) and Security Assertion Markup Language (SAML). SAML works best for traditional browser-based enterprise applications, while OIDC is designed for modern, API-first, mobile, and cloud-native systems. Choosing the right protocol impacts security, development effort, and scalability.
Understanding the differences between OIDC vs SAML helps teams select the protocol that best aligns with their environment, security needs, and development requirements.
OIDC: An Overview
Many teams search for “What is OIDC?” or “OpenID Connect vs OAuth2” to understand how OIDC modernizes authentication. OIDC is a lightweight identity layer built on top of OAuth 2.0, enabling applications to securely authenticate users using JSON, REST, and JWT tokens. While OAuth 2.0 focuses on authorization, OIDC specifically handles authentication.
Modern design principles
- Easy for developers to integrate using REST and JSON
- Works across mobile, native, IoT, and web applications
- Leverages compact JWT tokens for efficient validation
- Built for cloud-native and API-driven environments
Common use cases
- Authentication for iOS, Android, and other mobile apps
- Login for modern SPAs (React, Angular, Vue)
- Distributed cloud and microservice-based systems
- Consumer applications offering social logins
You can also opt for tools like Authgear that make implementing OIDC easier. This is done by providing a centralized, cloud-based identity platform with prebuilt support for modern apps and microservices.
SAML: An Overview
SAML is an older but widely trusted protocol used for federated identity and Single Sign-On. It was introduced in the early 2000s, when most applications were traditional, browser-based, and used inside corporate environments.
The main purpose of SAML was to help organizations securely share authentication details without forcing users to maintain separate passwords for every app.
Modern design principles
In SAML, the user doesn’t receive a token like a JWT. Instead, the system generates a SAML Assertion, which is an XML-formatted document that contains identity and optional authorization details.
This assertion is digitally signed by the Identity Provider (IdP), enabling the Service Provider (SP) to trust it without needing a direct verification call.
Common use cases
- Traditional and legacy web applications
- Internal workforce identity systems and HR platforms
- Business-to-business partner access
- Enterprise SaaS products such as Salesforce, Workday, or ServiceNow
Even for SAML-based systems, Authgear can act as a centralized identity provider. It bridges legacy enterprise systems with modern apps, giving teams a single platform to manage authentication across OIDC and SAML workflows.
How Are SAML and OIDC Similar?
SAML and OIDC are both modern identity federation standards designed to solve the same core business challenge: enable SSO across applications without forcing users to maintain separate credentials for each system.
They externalize user authentication to a trusted IdP and allow multiple applications (Service Providers or Relying Parties) to rely on the authentication result.
Here are the main similarities:
- Federation and SSO: Both allow users to authenticate once with a central IdP and access multiple applications without re-entering credentials.
- Browser-based redirects: Identity information is passed through redirects rather than direct credential exchanges, minimizing the risk of storing passwords in multiple systems.
- Token-based identity exchange: SAML uses XML assertions, and OIDC uses JWTs, but both securely convey user identity between the IdP and applications.
- Broad IdP support: Major identity providers, including Azure AD, Okta, Ping Identity, Auth0, Google, AWS Cognito, and ADFS, support both protocols.
- Standardized and mature: Both are open standards with extensive tooling, industry validation, and widespread enterprise adoption.
How the Protocols Work
Authentication flows vary between SAML and OIDC, influencing application design and integration complexity.
OIDC Flow: Modern Token-Based Authentication
OIDC, as part of the OIDC vs OAuth discussion, builds on OAuth 2.0. Its flow involves:
- The user accesses an application.
- The client redirects the user to the IdP’s authorization endpoint.
- The user authenticates.
- The client receives an authorization code, exchanged for an ID token (JWT) and optionally an access token.
- Tokens are validated, and the session is established
OIDC enables programmatic access for APIs and supports SPAs and mobile apps. It also incorporates security measures like PKCE, token expiry, and refresh tokens, which make it ideal for modern cloud-native applications.

The diagram depicts the OIDC authentication flow involving the User, Relying Party (RP), and Identity Provider (IdP). Rectangular boxes highlight key actions or stages, while arrows show the sequence of data exchanges and user interactions.
Numbered steps guide viewers through the process, from metadata exchange and user login to scope validation and access approval. Color coding clarifies roles: blue for RP activities, purple for scope-related exchanges, yellow for IdP actions, and green for redirections.
The layout majorly emphasizes the two-way communication between RP and IdP, illustrating how tokens and user consent flow through the system to establish a secure session.
SAML Flow: Enterprise-Friendly XML Assertions
SAML is primarily browser-based and is often used for workforce SSO. Its high-level flow is:
- The user accesses a service provider (SP).
- The SP redirects the user to the IdP for authentication.
- The IdP verifies credentials and returns a SAML assertion (XML document containing identity data).
- The SP validates the assertion and grants access.
SAML is particularly strong for enterprises requiring centralized audit and single logout. Understanding OIDC vs OAuth clarifies why OIDC is the preferred modern authentication standard, complementing OAuth 2.0’s authorization capabilities.
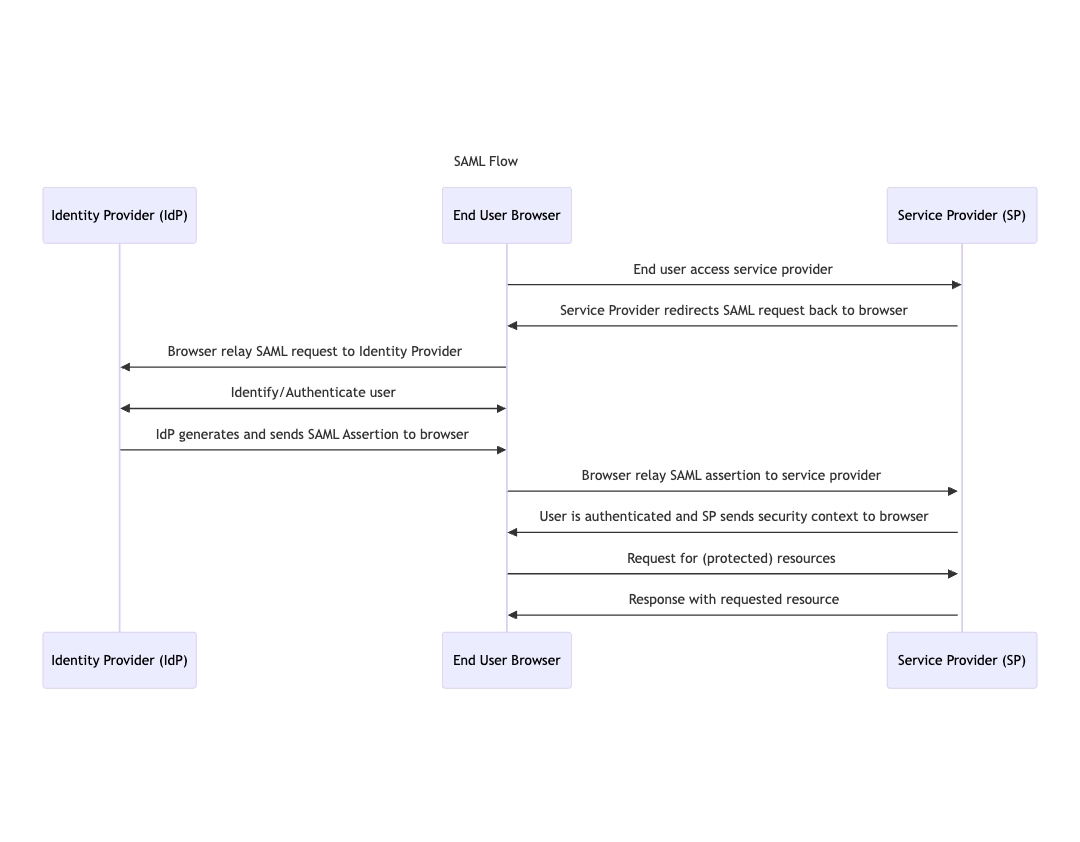
This diagram walks you through the SAML authentication flow in a logical sequence. It starts with the user trying to log in, shown by simple shapes that represent each key player: the service provider, the user, and the identity provider.
As you follow the numbered steps and arrows, you see how the service provider requests authentication, the identity provider verifies the user's identity, and then returns a SAML assertion.
At last, the service provider parses this assertion to make an access decision, either granting or rejecting access, all clearly highlighted for quick understanding. It's designed to blend clarity with essential technical terms, making the process easy to grasp at a glance.
OIDC vs SAML: A Clear Comparison
While both protocols enable SSO, OIDC vs SAML highlights differences in technology, token format, and developer experience that affect implementation and security.
Key Differences
SAML requires careful metadata and certificate handling, while OIDC simplifies discovery via well-known endpoints and JWKS. For developers familiar with OAuth 2.0, adopting OIDC is faster and easier.
Here’s a comparison table:
Security Considerations
Security is crucial when evaluating authentication protocols. Each has unique strengths and risks depending on the application type.
- SAML Security: SAML relies on XML signatures and certificates. Key risks include assertion replay and metadata tampering. Its audit-friendliness makes it suitable for highly regulated environments.
- OIDC Security: OIDC uses JWTs, PKCE, nonces, token expiry, and refresh tokens. Risks include token leakage and misconfigured redirect URIs. Comparing OAuth vs SAML illustrates OIDC’s advantages in modern web and mobile contexts.
Both protocols are secure when implemented properly. SAML is well-suited for regulated enterprise environments, while OIDC works best for modern, cloud-native applications - but careful token handling is essential.
With Authgear, you get centralized management that ensures tokens are securely handled and validated across both protocols.
Application Fit and Typical Use Cases
The right protocol depends on application type and ecosystem support. OIDC suits modern apps, while SAML remains relevant for legacy enterprise systems.
- OIDC: Cloud-native apps, SPAs, mobile apps, APIs, microservices; suitable for customer identity (CIAM).
- SAML: Legacy enterprise portals, ERP/HR systems, workforce SSO; strong audit and compliance.
Implementation Considerations
Implementation complexity, SDK availability, and metadata handling vary between protocols. Knowing these differences reduces errors and ensures secure integration.
- Libraries and SDKs
- OIDC is widely supported across Spring Security, Express.js, Next.js, React Native, Flutter, and most programming languages. SAML SDKs (e.g., OneLogin, Shibboleth, Spring SAML) require more setup and XML expertise.
- Metadata and Key Management
- SAML requires manual metadata exchange and certificate management. OIDC simplifies this with well-known endpoints and JWKS, making token validation and key rotation easier.
- Common Implementation Pitfalls
- Misconfigured SAML assertion lifetimes → login failures
- OIDC SPAs require PKCE → security risk if omitted
- Token storage in OIDC must be secure → prevent XSS attacks
- Certificate updates in SAML must be synchronized between the IdP and the SP
How To Choose the Right Protocol for Your Apps?
Deciding between SAML vs OIDC ultimately comes down to understanding your application types, user base, and long-term identity strategy. Both protocols provide secure Single Sign-On (SSO) and federated identity, but they are optimized for different environments and use cases.
When to Use OIDC
OIDC is the better choice for modern, cloud-first applications. Use it for:
- SPAs built with React, Angular, or Vue
- Mobile apps on iOS or Android
- API-first or microservice architectures
- Customer identity management (CIAM) and social login integrations
OIDC uses lightweight JSON Web Tokens (JWTs), REST APIs, and supports modern authentication practices like PKCE and token refresh.
Teams familiar with OAuth 2.0 find OIDC easy to implement using widely available SDKs and libraries. Its flexibility and modern design make it ideal for applications that need to scale quickly across devices and cloud environments.
When to Use SAML
SAML remains a strong choice for traditional enterprise applications. Use it for:
- Legacy web apps such as HR portals, ERP systems, and internal SaaS tools
- Workforce SSO where a centralized login is required
- Highly regulated environments that demand detailed audit trails
- Organizations relying on SAML-first IdPs like ADFS or Ping Identity
SAML uses XML assertions and robust signature-based validation, making it reliable for browser-based SSO and environments where compliance is critical. It is less suited for modern mobile apps or API-first systems.
Hybrid Approaches
Many organizations adopt a hybrid strategy: SAML for legacy enterprise apps and OIDC for new cloud-native or mobile systems. Over time, teams often migrate more services to OIDC to simplify authentication, improve user experience, and support modern development practices.
By evaluating your applications, user types, and long-term roadmap, you can select the protocol, or combination, that provides secure, scalable, and maintainable authentication for your organization.
Wrapping Up
Choosing between OIDC vs SAML doesn’t have to be complicated. If you’re building modern web apps, mobile apps, or APIs, OIDC makes integration easier and works well with today’s cloud environments.
For older enterprise systems, SAML is still reliable and trusted for security and compliance. Many organizations use both SAML for legacy apps and OIDC for new ones, so they can update systems without causing disruption.
If you want centralized identity management that works across microservices, mobile apps, and legacy systems, Authgear Cloud can simplify your authentication strategy, improve security, and give you peace of mind.
Start your free trial of Authgear today and unify identity management across all your applications.
FAQs
Can OIDC replace SAML entirely?
Not always. While OIDC is great for modern, API-driven systems such as APIs, SPAs, and mobile apps, SAML is still common in enterprises with legacy applications or strict compliance requirements. Many organizations use both SAML for older systems and OIDC for new ones.
How is SAML different from OAuth?
SAML is for authentication, meaning it checks who the user is. OAuth is for authorization, meaning it controls what the user can do. SAML uses XML assertions, and OAuth uses tokens.
Which is more secure, OIDC or SAML?
Both are secure when set up correctly. SAML is strong for enterprise SSO with auditing. OIDC is good for modern apps, but tokens and redirects must be handled carefully to stay safe.








